VAPT Services
Vulnerability Assessment & Penetration Testing
Aadit Technologies offers comprehensive VAPT (Vulnerability Assessment and Penetration Testing) services to identify and fix security weaknesses. Key benefits include: proactive risk mitigation, compliance with regulations (GDPR, HIPAA, PCI DSS), improved security posture, and reduced financial losses. Their VAPT process includes planning, scanning, testing, reporting, and remediation support. Contact Aadit Technologies in Bangalore for a free consultation.
Shield Your Business with Expert VAPT Services
In today’s interconnected digital landscape, cyber threats are more sophisticated and persistent than ever before. One unnoticed vulnerability can be exploited, leading to data breaches, financial losses, and reputational damage. Is your organization truly prepared to withstand the onslaught of modern cyberattacks? Do you know where your security gaps lie? At Aadit Technologies, we provide comprehensive Vulnerability Assessment and Penetration Testing (VAPT) services designed to proactively identify, assess, and remediate security weaknesses in your systems, applications, and networks. Our expert team of ethical hackers uses cutting-edge techniques and industry-leading tools to simulate real-world attacks, giving you a clear picture of your security posture and empowering you to take decisive action. Don’t wait for a breach to happen – take control of your security today with our tailored VAPT services and fortify your defenses against evolving cyber threats. With Aadit Technologies, you’re not just investing in security; you’re investing in peace of mind and the long-term success of your business. Our focus is on providing 360° Cyber Security solutions, specializing in Cloud, Security, GRC (Governance, Risk & Compliance), and AI/Automation, making us the ideal partner for all your security needs.
Ready to uncover your vulnerabilities?
Request a Free Consultation
What is VAPT & Why is it Essential?
VAPT, short for Vulnerability Assessment and Penetration Testing, is a comprehensive security testing approach that combines two crucial processes: Vulnerability Assessment and Penetration Testing. While both serve the common goal of identifying security weaknesses, they employ different methodologies and offer unique insights. A vulnerability assessment systematically scans your systems for known vulnerabilities, providing a prioritized list of potential weaknesses. On the other hand, penetration testing goes a step further by actively attempting to exploit those vulnerabilities to determine the extent of the damage an attacker could inflict. Together, they provide a holistic view of your security posture.
Why is VAPT Essential?
Proactive Risk Mitigation: Identify and fix vulnerabilities before attackers exploit them.
Compliance Requirements: Meet regulatory standards like GDPR, HIPAA, PCI DSS, and ISO 27001
Improved Security Posture: Strengthen your overall security defenses and reduce the risk of cyberattacks
Expert Incident Response: A structured process for containing, eradicating, and recovering from security incidents, led by experienced analysts.
Enhanced Business Reputation: Protect your brand image and customer trust.
Reduced Financial Losses: Prevent costly data breaches and downtime.
Read more about the importance of cybersecurity on CISA’s website.
Protect your business from potential threats.
Request a Free Consultation
Our Comprehensive VAPT Services
At Aadit Technologies, we offer a comprehensive suite of VAPT services tailored to meet the unique needs of your organization. Our experienced team of certified security professionals employs industry-leading methodologies and advanced tools to deliver accurate and actionable results.
Penetration Testing
External Network We simulate attacks from outside your network to identify vulnerabilities in your publicly accessible systems, such as firewalls, routers, and web servers.
Internal Network Penetration Testing
We assess the security of your internal network to identify vulnerabilities that could be exploited by malicious insiders or attackers who have already gained access.
Web Application Penetration Testing
We identify vulnerabilities in your web applications, such as SQL injection, cross-site scripting (XSS), and authentication flaws.
Mobile Application Penetration Testing
We assess the security of your mobile applications to identify vulnerabilities that could compromise user data or device security.
Cloud Security Assessment
We evaluate the security of your cloud infrastructure and applications, identifying misconfigurations, vulnerabilities, and compliance gaps.
Wireless Network Penetration Testing
We assess the security of your wireless networks to identify vulnerabilities that could allow unauthorized access to your network.
Social Engineering Assessment
We simulate social engineering attacks to assess the awareness and susceptibility of your employees to phishing, pretexting, and other social engineering tactics.
Vulnerability Scanning and Reporting
We provide automated vulnerability scanning services to identify known vulnerabilities in your systems and applications, along with detailed reports outlining the findings and recommendations.
Learn more about our VAPT services by visiting our Cybersecurity Services page
Interested in a specific VAPT solution?
Request a Free Consultation
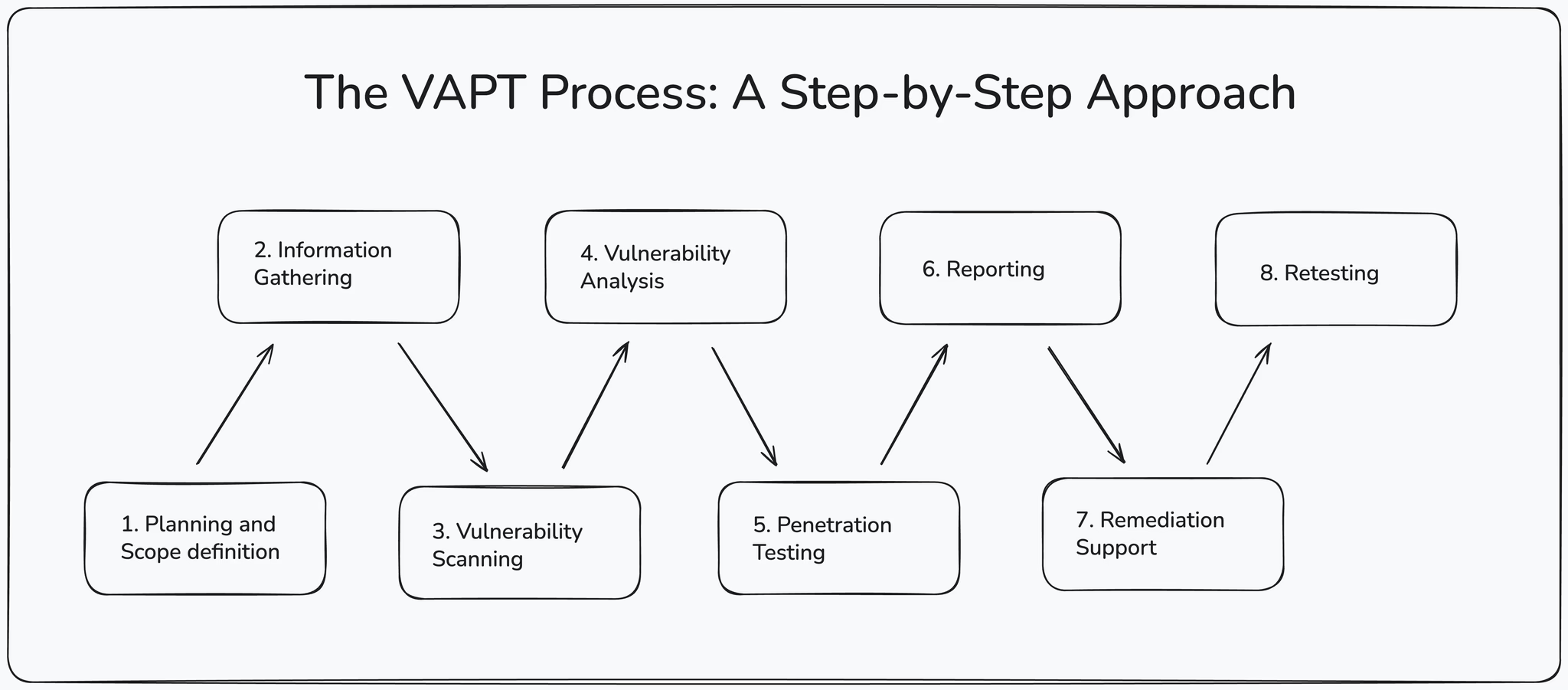
The VAPT Process: A Step-by-Step Approach
Our VAPT process is a structured and methodical approach designed to deliver comprehensive and actionable results. We work closely with you throughout the entire process to ensure that our testing aligns with your business objectives and security priorities.
Planning and Scope Definition
We work with you to define the scope of the VAPT assessment, including the systems, applications, and networks to be tested.
Information Gathering
We gather information about your environment, including network topology, system configurations, and application architectures.
Vulnerabilty Scanning
We use automated tools to scan your systems for known vulnerabilities.
Vulnerability Analysis
We analyze the results of the vulnerability scans to identify and prioritize the most critical vulnerabilities
Penetration Testing
We attempt to exploit the identified vulnerabilities to determine the extent of the damage an attacker could inflict
Reporting
We provide a detailed report outlining the findings of the VAPT assessment, including a prioritized list of vulnerabilities, remediation recommendations, and a summary of the overall security posture
Remediation Support
We provide guidance and support to help you remediate the identified vulnerabilities
Retesting
We retest the remediated vulnerabilities to ensure that they have been successfully resolved.
See how our VAPT process can protect your business.
Request a Free Consultation
Benefits of Choosing Aadit Technologies for Your VAPT Needs
When you choose Aadit Technologies for your VAPT services, you benefit from our expertise, experience, and commitment to delivering exceptional results.
Here are some of the key benefits of working with us:
Experienced and Certified Professionals: Our team consists of highly skilled and certified security professionals with years of experience in vulnerability assessment and penetration testing.
Industry-Leading Methodologies: We employ industry-leading methodologies and best practices to ensure comprehensive and accurate testing.
Advanced Tools and Technologies: We use the latest tools and technologies to identify and exploit vulnerabilities.
Customized Solutions: We tailor our VAPT services to meet the unique needs of your organization.
Actionable Reporting: We provide detailed and actionable reports that clearly outline the findings of the VAPT assessment and provide practical remediation recommendations.
Remediation Support: We provide guidance and support to help you remediate the identified vulnerabilities.
Competitive Pricing: We offer competitive pricing without compromising on quality or service.
360° Cyber Security Solutions: We specialize in providing comprehensive security solutions, ensuring all aspects of your business are protected.
Request a Free Consultation
Compliance and Standards
Our VAPT services help you meet various compliance requirements and industry standards, including:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
PCI DSS (Payment Card Industry Data Security Standard)
ISO 27001 (Information Security Management System)
SOC 2 (System and Organization Controls 2)
By partnering with Aadit Technologies for your VAPT needs, you can demonstrate your commitment to security and compliance, reducing your risk of fines and penalties.
Ensure your business is compliant with industry standards. Discuss VAPT Compliance
Request a Free Consultation
Pricing
Our VAPT service pricing varies based on the scope of the assessment, the complexity of your environment, and the level of testing required. We offer flexible pricing models to meet your budget and requirements.
Example Pricing Tiers:
Basic VAPT Package
Starting at ₹50,000 (INR) – Ideal for small businesses with limited IT infrastructure
Request a Free Consultation
Premium VAPT Package
Starting at ₹2,50,000 (INR) – Designed for large enterprises with complex IT environments and stringent security requirements.
Request a Free Consultation
Standard VAPT Package
Starting at ₹1,00,000 (INR) – Suitable for medium-sized businesses with moderate IT complexity.
Request a Free Consultation
Ready to take the next step in securing your business? Contact Aadit Technologies today to discuss your VAPT needs and schedule a free consultation.
Contact Us
Don't Wait for a Breach
Act Proactively.
“A single vulnerability can cost millions. Prevention is power.”
Start securing your business today.
Request a Free Consultation
Discover your services,
see how we can help you.
FAQs
Have more questions about how Aadit’s VAPT can protect your specific business?
Contact us today for a personalized discussion
What is VAPT?
VAPT stands for Vulnerability Assessment and Penetration Testing. It’s a comprehensive security testing approach that combines vulnerability assessment (identifying potential weaknesses) and penetration testing (actively attempting to exploit those weaknesses) to provide a holistic view of your security posture.
Why is VAPT important?
VAPT is crucial for proactively identifying and mitigating security risks. It helps organizations comply with regulations, improve their security posture, protect their brand reputation, and reduce the risk of financial losses due to cyberattacks.
How does VAPT work?
The VAPT process typically involves planning and scope definition, information gathering, vulnerability scanning, vulnerability analysis, penetration testing, reporting, remediation support, and retesting. This structured approach ensures comprehensive and accurate assessment of your security defenses.
What are the different types of VAPT?
Aadit Technologies offers various VAPT services, including external network penetration testing, internal network penetration testing, web application penetration testing, mobile application penetration testing, cloud security assessment, wireless network penetration testing, and social engineering assessment.
What are the benefits of VAPT?
The benefits of VAPT include proactive risk mitigation, compliance with regulations, improved security posture, enhanced business reputation, reduced financial losses, and a better understanding of your organization’s security weaknesses.
How often should I conduct VAPT?
It’s recommended to conduct VAPT at least annually, or more frequently if you’ve made significant changes to your IT infrastructure, deployed new applications, or experienced a security incident. Regular VAPT helps you stay ahead of evolving cyber threats
What compliance standards does VAPT help with?
VAPT can help you meet various compliance requirements, including GDPR, HIPAA, PCI DSS, ISO 27001, and SOC 2. By conducting VAPT, you demonstrate your commitment to security and compliance, reducing your risk of fines and penalties.
How much does VAPT cost?
The cost of VAPT varies depending on the scope of the assessment, the complexity of your environment, and the level of testing required. Contact Aadit Technologies for a customized quote tailored to your specific needs
