Now Hiring: Are you a driven and motivated 1st Line IT Support Engineer?
A Security Operations Center (SOC) investigates, monitors, detects, prevents and responds to cyber security threats and attacks round the clock – 24/7. The Security Operations Center aims to protect a company and or an entity against existing or new emerging cyber threats and attacks. The approach of SOC basically comprises of people, processes, and technology with a primary focus on managing, enhancing and building the company’s security posture and overall cyber security health.
With expertise and experience in offering advanced, dynamic, reliable and dependable cybersecurity services, Aadit Technologies has served and secured IT infrastructure as well as valuable IT assets for many Indian industries, and companies across the world.
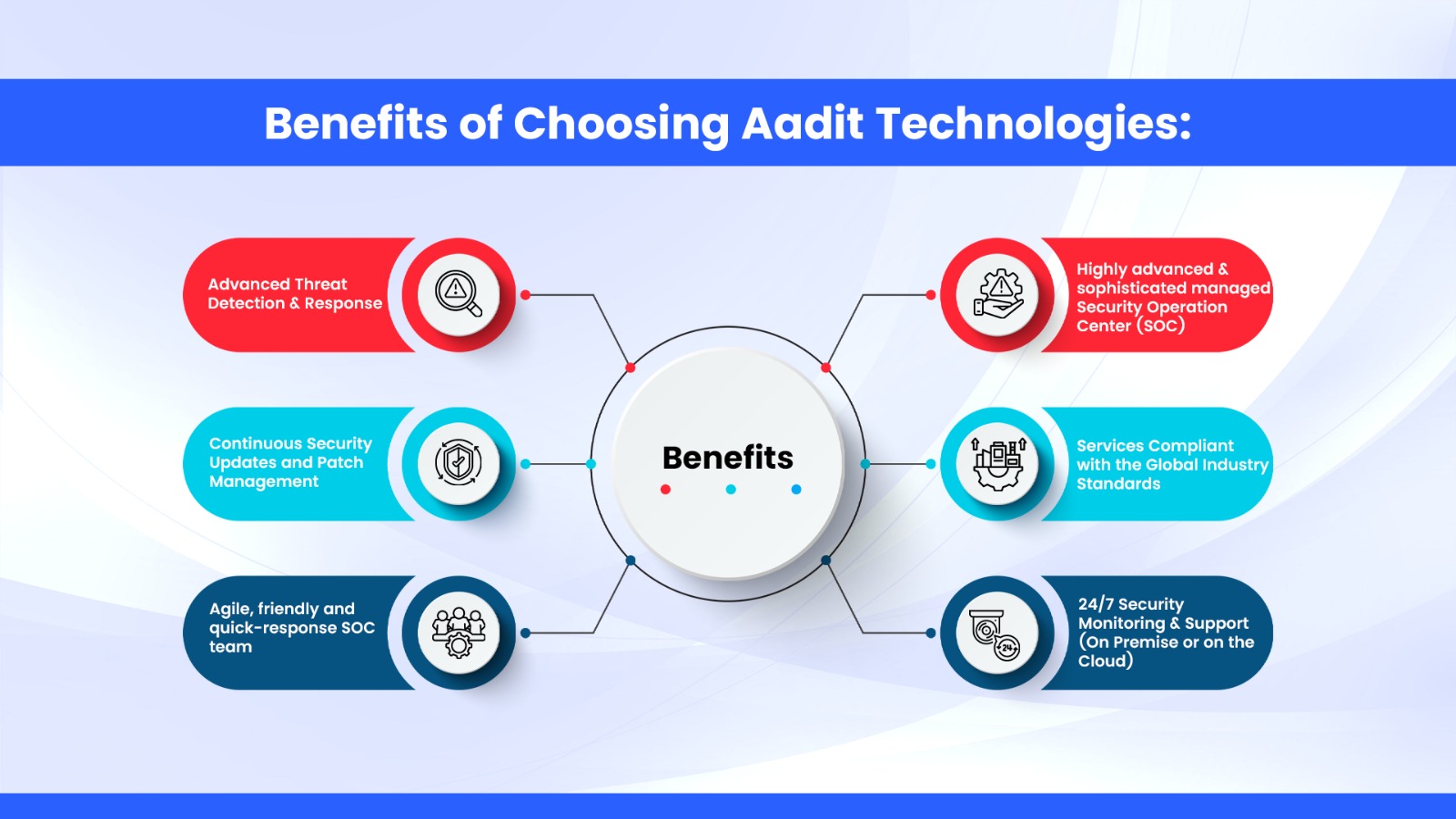
Aadit Technologies Security Operations Center team has a collective industry experience and power packed expertise of over 50 man-years. For our clientele across India and the world, Aadit Technologies has emerged as the “Go-To-Company” to troubleshoot existing and new emerging cyber security threats by securing their valuable IT infrastructure and assets with our time-bound, ultra-modern and cost-effective cyber security solutions.
For our customers, Aadit Technologies has proved to be a catalytic agent and a game-changer in securing our client’s businesses, in turn boosting their finances by protecting their valuable IT infrastructure and assets from the ever-emerging cyber security threats in this new age of disruptive fourth industrial revolution.
Know About SOC’s Workings:
SOC’s primary functionality and workings focus on alerting and continuous monitoring of any vulnerabilities and anomalies in the client’s network. Its steady focus remains on collecting and analyzing critical data and remediating any suspicious activities and threats. If detected these threat data are precisely collected from multiple sources like intrusion detection and prevention systems, firewalls, security information and event management (SIEM) systems, and Aadit Technologies expert threat intel.
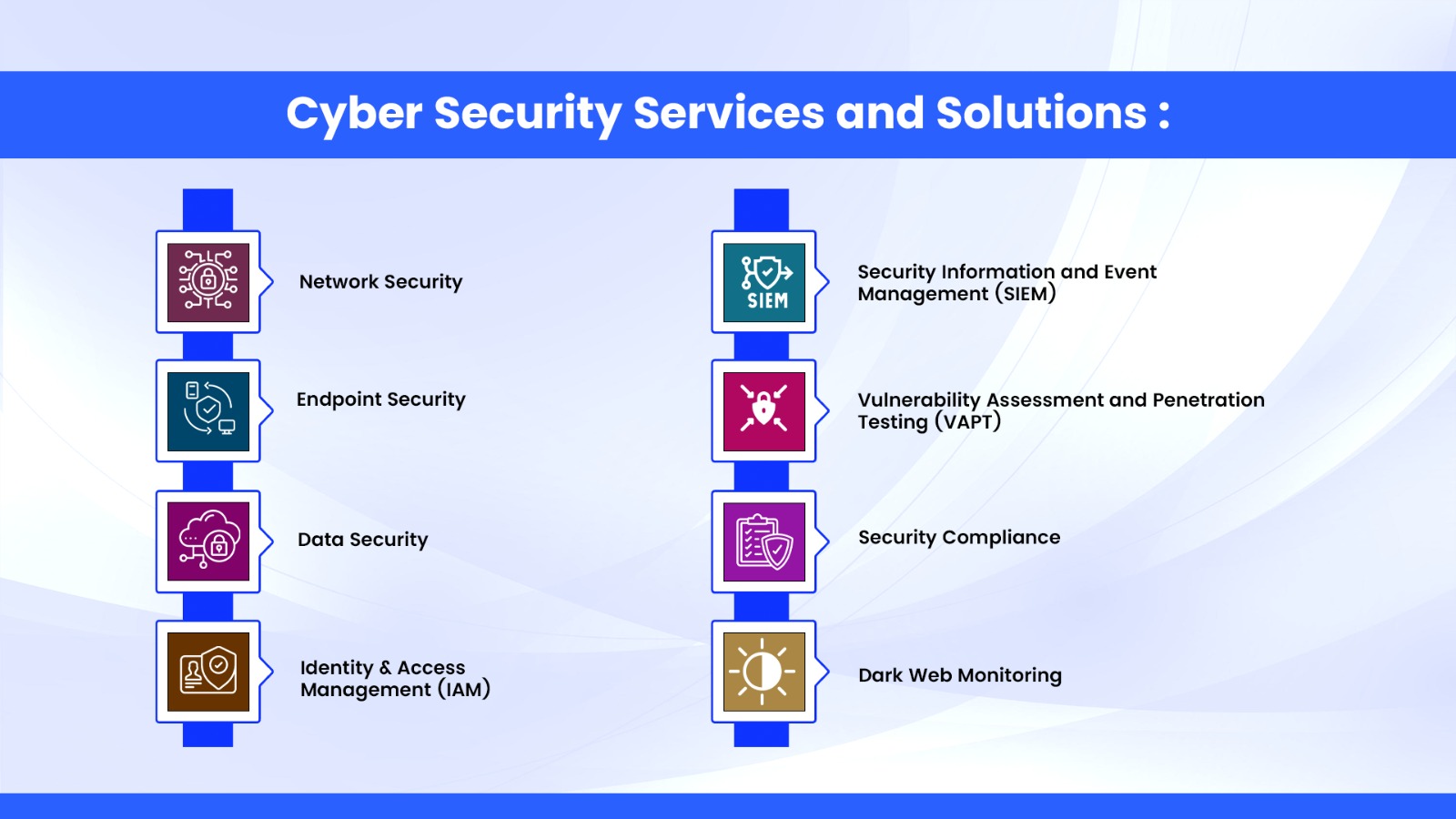
Critical Functions Executed by SOC:
Utilizing Existing Resources – the Security Operations Center primarily utilizes two types of resources – the various security applications, devices and processes; and secondly security tools used to defend and protect.
The SOC aims to Protect – the Security Operations Center aims to get a total 360-degree view of the security network’s threat landscape with an all-inclusive focus on the numerous types of endpoints, servers, tools and software’s including third party services, if any.
At Aadit Technologies, the SOC team implements effective preventative measures that have two main types:
Preparation: At Aadit Technologies the Security Operations Center team stays on top and forward looking with their research on new and emerging security innovations and inventions as well as with an eagle’s eye on the cybercrime world and its remediations.
Preventative Maintenance: For preventative maintenance, Aadit’s Security Operations Center team focuses on thwarting any potential attacks on the regularly maintained existing and upgraded security systems.
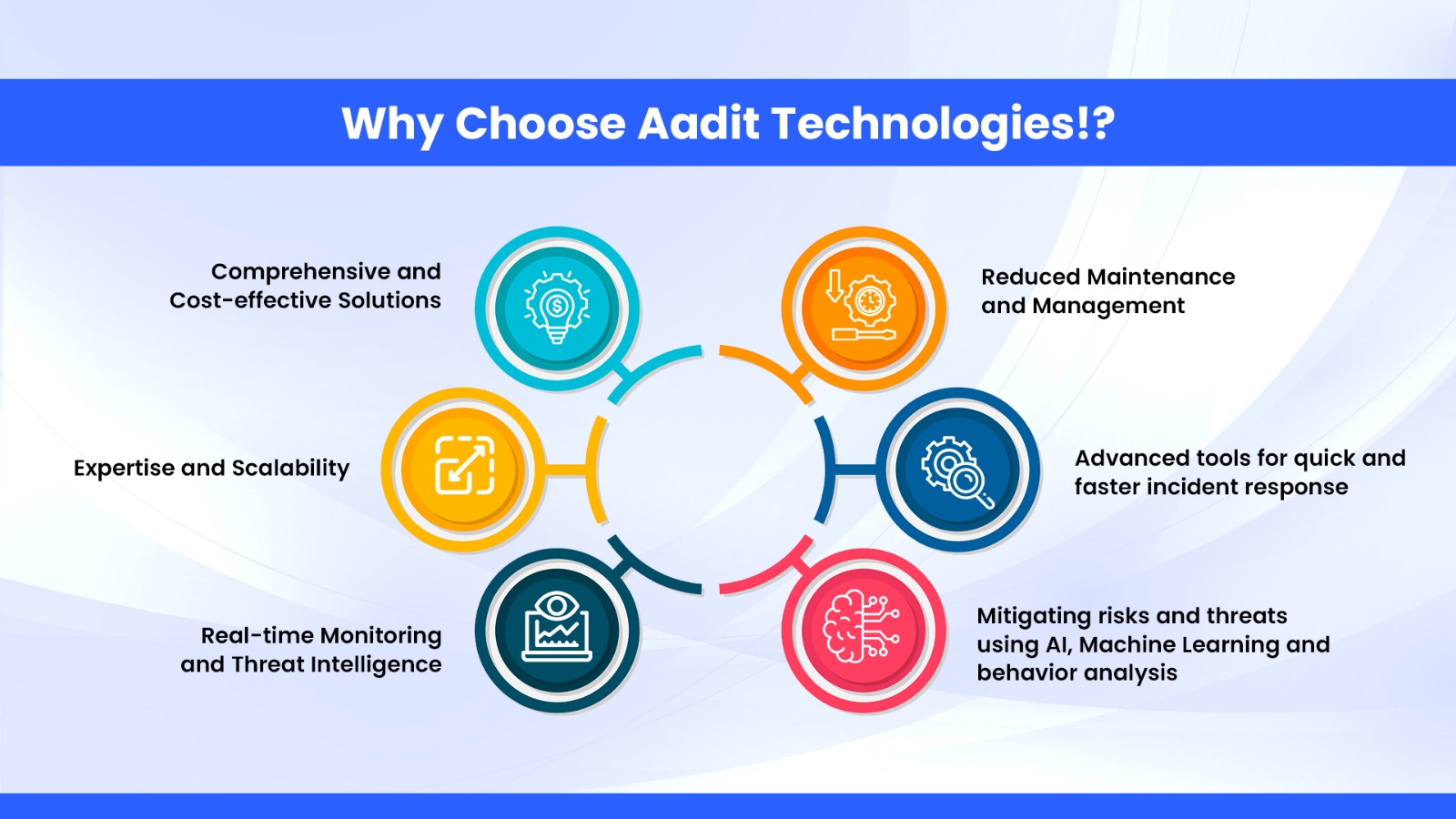
24/7 Proactive Monitoring: To ensure total security protection, Aadit Technologies SOC team proactively monitors and scans the network for any possible attacks, threats, and/or suspicious erratic activities. Aadit Technologies SOC team works 24/7 to mitigate risks and threats by employing AI, Machine Learning and behavior analysis empowered with tools like SOAR, SIEM, EDR, or an XDR. This approach by Aadit’s SOC team saves valuable time by minimizing human analysis and errors.
Remediation and Recovery: Post any threat incident, Aadit’s Security Operations Center team executes plans to remediate, recover the systems, critical data and any infected, lost or compromised data. The SOC team focuses in reinstating, restarting and reconfiguring all the endpoints, systems and physical assets, in the process securing and deploying backup plans to evade any further troublesome ransomware attacks.
Threat Response: In the event any threat is detected, Aadit’s SOC team as the first responder springs into action, and performs exigent remediation like shutting down systems/servers/assets, isolating endpoints, terminating harmful processes, detecting and isolating infected files, ensuring minimal impact on business continuity and losses.
Log Management: Aadit’s Security Operations Center team are experts in log management for all the network activity of the entire business. The critical logs and network activity, detected helps reveal the existence and extent of threats, and simultaneously are used for remediation and forensics in the aftershock of any threat or attack. Applications, endpoints, OS, firewalls all of which produce their own unique internal logs are used to aggregate and correlate the data log feeds.
Alert Ranking and Management: Aadit Technologies SOC team uses triage of monitoring tools to issue security alerts in turn empowering the SOC team to sort and prioritize the probable threats and quell false alarms.
Security Refinement and Improvement: Till date the world has recorded over 1000 types of ransomware attacks. As bad actors on the dark web the Cybercriminals are ever inventing newer tools and techniques to effect their nefarious plans. To stay a step ahead of such Cybercriminals, Aadit’s SOC team implements advanced techniques and global industry standards for continuous security refinement and improvement.
Investigating Root Cause: After any incident, Aadit’s Security Operations Center team analyses and precisely identifies what, when, how and why aspects of the security analysis. All through such forensic investigation, the SOC team uses the critical data and relevant information to trace the root cause of the incident. Once done, Aadit’s Security Operations Center team ensures such incidents do not occur again.
Compliance Management: Aadit Technologies SOC team follows Global Industry Standards and best practices governed for the security compliance requirements. Aadit’s SOC team frequently audits the systems to ensure compliance with regulations issued by industry and or governing authorities or bodies.
Any small, medium or big enterprise ready to implement SOC can choose from the following models:
The essential roles of Aadit’s SOC team consists of different tiers of SOC analysts, experts and dedicated managers each owns a specific skill set.
Tier 1 — Triage Specialist:
Tier 1 analysts are experts at collecting raw security data, reviewing alarms and alerts. Being a specialist at managing and configuring monitoring tools, the triage specialist identifies whether it’s a false alert or a real issue. If anomalies occurring at Tier-1 level are not resolved, they are escalated to tier 2 analysts.
Tier 2 — Incident Responder:
At the tier 2 level, analysts review the higher-priority security incidents escalated by triage specialists (tier-1) and do a more deep-dive and in-depth assessment using threat intelligence. Tier 2 – incident responders design and implement strategies to contain and recover from an incident. If a tier 2 analyst faces major issues with identifying or mitigating an attack, the incident is escalated to tier 3 experts.
Tier 3 — Threat Hunter:
In Aadit’s SOC team the most experienced workforce are Tier 3 analysts. Major incidents escalated by the incident responders are handled by Tier 3 – Threat Hunters. The most important responsibility for threat hunters is to proactively identify unknown possible threats, security gaps and vulnerabilities. Further, any critical security alerts, threat intelligence, and other security data provided by tier 1 and tier 2 analysts are reviewed by tier 3 threat hunters.
SOC Manager
SOC managers supervise the security operations team. They provide technical guidance, support in hiring, training and evaluating team members; creating processes; assessing incident reports; and developing and implementing necessary crisis communication plans. They also oversee the financial aspects of a SOC, support security audits, and report to the chief information security officer (CISO) or a respective top-level management executive.
In addition to the above tiered roles, other technical and specialty roles exist, like:
Malware Analysts or Reverse Engineers
Are experts who respond to sophisticated threats by reverse engineering malware to help inform incident investigations, provide threat intelligence to Aadit’s SOC team, and improve future detection and response efforts.
Threat Hunters
At Aadit’s SOC team threat hunters proactively hunt for threats inside the enterprise.
Forensics Specialists or Analysts
Are specialists in Aadit’s SOC team who research and investigate cybercrimes linked to IT systems, security networks and digital forensic proofs.
Vulnerability Managers
At Aadit’s SOC team vulnerability managers assess, identify, manage, report on, and remediate vulnerabilities across OS, endpoints, workloads and systems.
Consulting Roles
For consulting roles at Aadit’s SOC team, the important roles are Security Architect (SA) and Security Consultant. The SA plans, researches and designs a robust security infrastructure within an enterprise. Whereas, security consultants research security standards, security best practices and security systems.
Aadit’s SOC team are responsible for a wide range of security-related activities, including proactive monitoring, incident response, recovery, and remediation activities, and also compliance with global industry standards.
Proactive Monitoring:
Another term for proactive monitoring is threat monitoring, it includes critical log file analysis. Logs can come from system assets or from network resources, such as routers, firewalls, intrusion detection system (IDS) and email applications. Aadit’s SOC team works with various resources that includes IT workers, technicians, and also artificial intelligence (AI) and machine learning tools.
Incident Response and Recovery:
Aadit’s SOC team communicates and coordinates on enterprises ability to take exigent steps and mitigate enormous damages; to recover ASAP and to keep business running post an incident.
Remediation Activities:
Aadit’s SOC team provides data-driven analysis that empowers an enterprise to address vulnerabilities and fine tune security monitoring and alerting mechanisms. Remediating existing cybersecurity is a prime responsibility of Aadit’s SOC team.
Compliance:
Enterprises need a SOC to help ensure that they are compliant with important security standards and best practices, such as the General Data Protection Regulation (GDPR), the NIST Cybersecurity Framework (CSF), and ISO 27001x.
Coordination and Context:
Aadit’s SOC team helps an enterprise coordinate disparate elements and services and provide visualized, useful information. Part of this coordination is the ability to provide a helpful, useful set of narratives for activities on the security network.
An expert bunch of personnel, Aadit’s SOC team size converges based on the enterprise and industry’s needs providing hi-tech advantages, benefits and services. Aadit’s SOC team having a collective industry experience of over 50 man-years, the roles and responsibilities tend to remain the same.
Prevention and detection:
Aadit’s SOC team knows very well that in the cyber-security domain, pro-active approach towards prevention of cyber-attacks proves to be highly effective than reactive approach. Instead of reactively responding to the incident that occurred Aadit’s SOC team acts as first responders to monitor and troubleshoot 24/7. This pro-active approach of Aadit’s SOC team enables detection of malicious cyber activities on the network and nullifies them ASAP.
Deep-dive Investigation:
Aadit’s SOC team while operating in the investigation stage, deep-dive into the investigation analyzing suspicious activities, nature of the threat, type of cyber-attack, and the extent of damaging impact on the IT infrastructure, systems, network, and assets.
Before any further collateral damage causes a cascading effect on the enterprise’s business, IT infrastructure and financial health, Aadit’s SOC analysts identify and perform an in-depth triage on the various types of ransomware incidents, by understanding how these malicious attacks occur and transpire. Aadit’s SOC analysts combine their vast domain-expertise, research on the strengths and weaknesses of the network attacked, by conjoining the latest global threat intelligence that aids in revealing the cyber attacker’s techniques, tools, and trends thereby enabling to perform an effective and robust triage.
24/7 Response:
Post investigation and forensics study, Aadit’s SOC team coordinates a systematic response to remediate the security issue. Acting as the first responder and on confirmation of the incident, Aadit’s SOC team starts performing actions like isolating endpoints, OS, systems, eliminating harmful processes, preventing them from re-occurring, locking and deleting files, and applying AI & ML enabled security practices. Post an incident occurrence, the primary objective of Aadit’s SOC team is to restore systems and assets, as well as, aim to totally recover compromised or lost data, critical to the enterprise’s sustainability.
A SOC can empower small, medium, and large scale enterprises with manifold benefits like:
Aadit Technologies SOC-as-a-Service (SOCaaS) Security Delivery Model
When a 3rd party vendor operates and maintains a fully managed SOC on a subscription basis, it is primarily entailed as SOC-as-a-Service (SOCaaS) Security Delivery Model.
Aadit Technologies SOC-as-a-Service (SOCaaS) Security Delivery Model is all-inclusive of the 360 degree security functions performed by the traditional in-house SOC. This delivery model includes incident investigation and response; threat detection and intelligence; network monitoring; reporting; log management; risk and compliance et-all. The 3rd party vendor also becomes responsible for all the people, processes and technologies required to enable this security delivery model and provide non-stop 24/7 support.
Security information and event management (SIEM)
Aadit’s SOC team makes use of the most important and key tools like the cloud-based SIEM solution. SIEM’s functionality is to aggregate data from numerous security solutions and log files. Aadit’s SOC team makes use of new and advanced threat intelligence and AI/ML. These tools help SOC team detect evolving cyber threats, expedite the incident response, and nullify attacks planned by the cyber criminals.
Security orchestration, automation, and response (SOAR)
For more in-depth investigation and hunting Aadit’s SOC team makes use of SOAR that automates recurring and predictable response, remediation tasks, freeing up time and resources.
Extended detection and response (XDR)
Providing simplified solutions, XDR is a Saas tool that offers holistic, optimized security by integrating security products and critical data. Aadit’s SOC team makes use of XDR which broadens the scope of security, integrating protection across a wider range of products, including an enterprises systems, OS, endpoints, servers, cloud applications, emails, and other adjuncts.
Firewall
Aadit’s SOC team are aware that based on security rules defined by the SOC the firewall monitors traffic to and from the security network, allowing or blocking suspicious traffic on the network.
Log Management
Aadit’s SOC team exclusively uses logs which provide information about critical network activity. A log management solution included as part of SIEM, logs all the alerts coming from every piece of software, hardware, and endpoint functioning in the enterprise.
Vulnerability Management
Aadit’s SOC team uses vulnerability management tools that scan the network to identify any vulnerabilities that the cyber-criminal could exploit.
User and entity behaviour analytics
Aadit’s SOC team makes use of various modern and advanced AI & ML security tools that’s exclusively used to analyze critical security data collected from various devices, entity behavior analytics, to ensure normalcy of the networks, and enterprises valuable IT infrastructure and assets.
Security Operations Center Challenges
Skills Shortage
There’s a global skills shortage in the cyber-security industry. If an enterprise cannot hire new personnel with security skills then it becomes imperative to train existing professionals to effectively combat the challenges and ever-emerging new threats posed by cyber criminals.
Lack of Adequate Tooling
Systems migrated from the data center to the cloud, edge computing, the internet of Things (IoT), and remote work lack adequate tooling. Aadit’s SOC team while at the incident premises has encountered this inadequacy of having adequate tools to visualize the system or to intervene in the security premises.
Alert Fatigue
To limit alert fatigue and maintain sustainable SOC operations, tools that correlate alerts across systems help identify false positives, and effectively detect threats that are critical to the sustenance and normalcy of security networks.
Budget Not Planned According to Risk
Aadit’s SOC team is aware that inadequate budgets do not allow the SOC to address entire cyber risks facing the enterprise. In today’s highly vulnerable and unstable cyber landscape it has become critical to perform risk assessment, and allocate SOC budget suitably to address these new emerging cyber risks.
Process Latency
In the present day industrial 4.0 revolution, IT eco-system are changing at a feverish pitch, which calls for adequate changes to SOC processes that primarily have two aspects:
Aadit’s SOC team is aware that security systems tend to create latency because SOC processes do not evolve fast enough to keep pace with the ever evolving changes in the IT landscape.
Secondly, human beings can create latency because of inability to adapt to the new emerging technologies, both in terms of advanced hi-tech security tooling and the ever changing IT landscape.
Security Operations Center Best Practices
Aadit’s SOC team follows global industry standards and best practices to make SOC efficient and effective.
Going Beyond Traditional and On-Premise Environments
The new age mission critical systems are migrating to the cloud environment and has become ubiquitous for enterprise’s sustainable survival. Organizations need to visualize at 360 degree and monitor new emerging hitech-systems such as the public cloud, server-less applications, and Kubernetes.
Collect as Much Data as Possible
Aadit’s SOC team always make use of threat intelligence, AI/ML behavioral analysis, and other advanced methods collate as much data as possible. This contextual data helps isolate unknown and evasive cyber-threats that might be over-looked by traditional security tools.
Leverage Advanced Analytics
Aadit’s SOC team makes use of high degree of automation to prioritize, analyze, and respond to security alerts. Modern security technologies such as extended detection and response (XDR), security automation and orchestration (SOAR), and user and entity behavioral analytics (UEBA), greatly help augment human intelligence with advanced AI analytics based on machine learning.
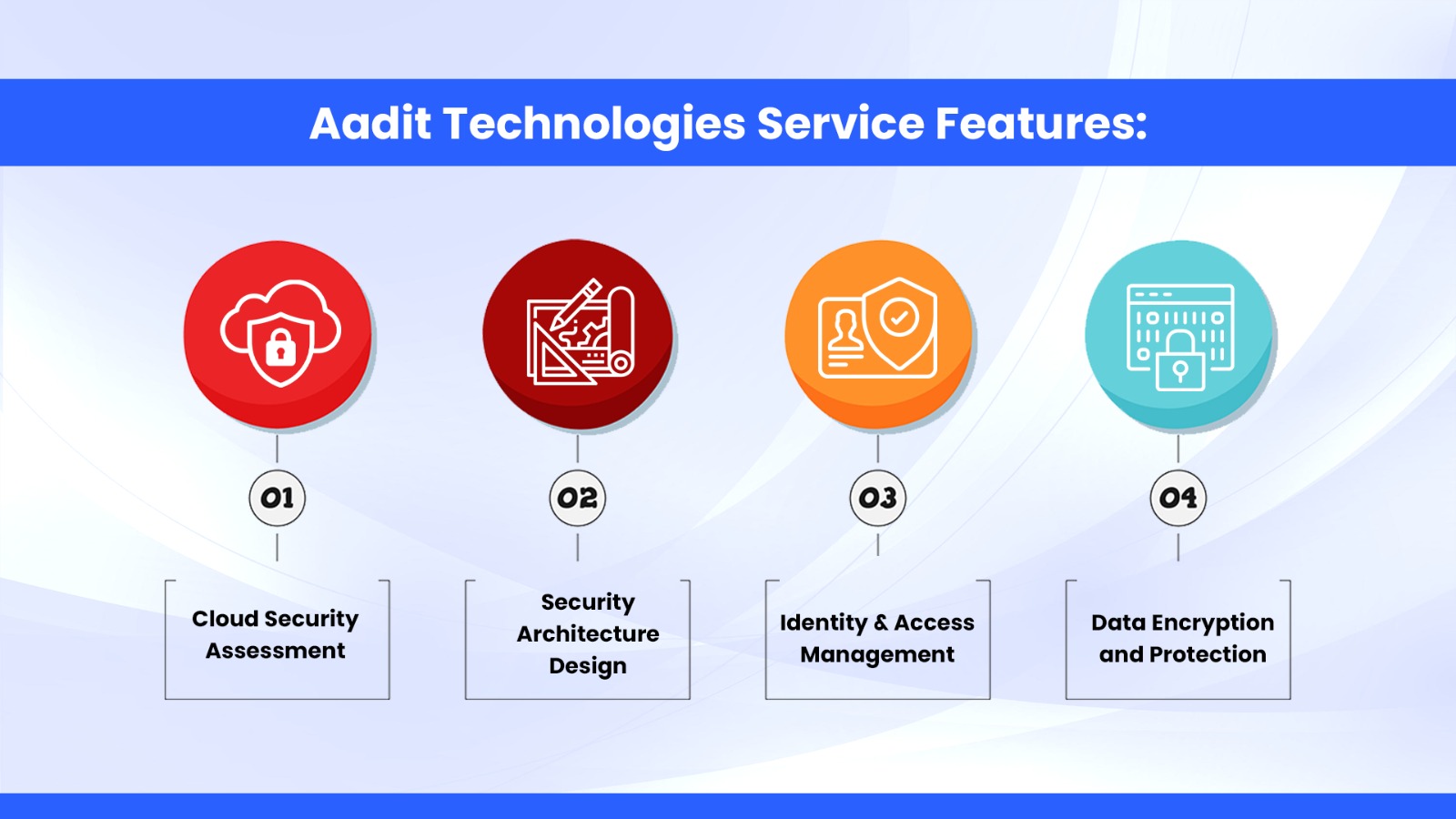
Security as a Service (SECaaS) is a cloud-based security model where security services are delivered over the internet by a third-party provider. Unlike traditional security solutions that require on-premises hardware and software, SECaaS offers scalable and flexible security solutions on a subscription basis. It includes a wide range of security services, such as threat detection, antivirus, firewall, data encryption, identity and access management, and more. SECaaS allows businesses to outsource their security needs, reducing the burden of managing complex security infrastructures and providing the agility to respond to rapidly evolving threats.
Yes, SECaaS is designed to cater to businesses of all sizes, from small startups to large enterprises. Its scalability and flexible subscription-based pricing model make it accessible and cost-effective for organizations with varying security requirements. Small businesses can benefit from SECaaS as it provides enterprise-grade security without the need for substantial upfront investments in hardware and expertise. Similarly, larger organizations can leverage SECaaS to complement their existing security infrastructure and enhance protection across distributed systems and remote locations.
Security as a Service providers employ a multi-layered approach to safeguarding your data and operations. They implement state-of-the-art security technologies, such as advanced threat detection, data encryption, intrusion prevention systems, and secure web gateways, among others. Additionally, SECaaS providers have teams of skilled security professionals who continuously monitor and respond to potential threats in real-time. They stay updated with the latest security trends, ensuring that your organization is protected against emerging threats. With SECaaS, you can have peace of mind knowing that your data and operations are safeguarded by a dedicated and expert security team.